And No, It Won’t Be Patched Before The Mid Terms.
J. Alex Halderman, Professor of Computer Science and Engineering at the University of Michigan, claims to have identified a critical privacy flaw in the election infrastructure sold by Dominion Voting Systems in the United States.
Halderman, a non-partisan analyst whose work has been cited by both left and right wing news sources, shared the website DVSorder.org on his social media channels on Friday.
1/ Colleagues and I have found a serious privacy flaw that affects Dominion ICP and ICE ballot scanners. We’ve already informed Dominion, CISA, EAC, and state officials, and we’ve created a site to help officials and the public understand the issue:https://t.co/ErwqtixOVC
— J. Alex Halderman (@jhalderm) October 14, 2022
What Is Affected and Where?
DVSorder is a privacy flaw that affects Dominion Voting Systems (DVS) ImageCast Precinct (ICP) and ImageCast Evolution (ICE) ballot scanners, which are used in parts of 21 states. Under some circumstances, the flaw could allow members of the public to identify other peoples’ ballots and learn how they voted.
The states potentially affected are: California, Alaska, Minnesota, Arizona, New Mexico, Kansas, Missouri, Illinois, Florida, Georgia, Tennessee, Virginia, New Jersey, New York, Ohio, Michigan, Wisconsin, Iowa, Vermont, Massachusetts, and Pennsylvania, as well as the territory of Puerto Rico.
Can This ‘Flip the Votes’?
The researchers explain:
This vulnerability is a privacy flaw and cannot directly modify results or change votes. Nevertheless, the secret ballot is an important security mechanism, and some voters—especially the most vulnerable in society—may face real or perceived threats of coercion unless the privacy of their votes is strongly protected.
Read Full Article on TheNationalPulse.com
Read J. Alex Halderman Tweets Series Below:
1/ Colleagues and I have found a serious privacy flaw that affects Dominion ICP and ICE ballot scanners. We’ve already informed Dominion, CISA, EAC, and state officials, and we’ve created a site to help officials and the public understand the issue: DVSorder.org
2/ We call the flaw DVSorder. It’s a privacy vulnerability, so it *cannot* directly modify results or change votes. However, under some circumstances, it could allow members of the public to identify other peoples’ ballots and learn how they voted.
3/ Many people don’t care if others know how they voted, but the secret ballot is an important security mechanism, and some voters—especially the most vulnerable in society—may face real or perceived threats of coercion unless the privacy of their votes is strongly protected.
4/ DVSorder is unusual in that it doesn’t require exotic skills or special access to find and exploit, only public information. Fortunately, now that we know about the problem, election officials have time to prevent it from affecting voters in the midterms.
5/ The problem has to do with ballot-level election data, such as cast-vote records (data with the votes from each ballot) and ballot images (scans of each ballot). Many localities post such data as a form of public transparency, e.g.: https://sfelections.sfgov.org/june-7-2022-election-results-detailed-reports
6/ In other jurisdictions, ballot-level data is treated as a public record, and there has been a surge in FOIA requests for it: https://www.washingtonpost.com/nation/2022/09/11/trump-election-deniers-voting/
People have used FOIA requests across the country to assemble data repositories like this: https://ordros.com/cvr/index.html
7/ To protect privacy, ballot-level data is supposed to be randomly shuffled, but the DVSorder flaw makes it possible for anyone to unshuffle data from Dominion ICP and ICE scanners and learn the order the ballots were cast.
This can sometimes be used to learn how people voted.
8/ (a) For example, scanners usually display a count of ballots cast. I can note the count when I vote, and if my wife uses the scanner next, I’ll know her ballot number too. If my locality releases vulnerable CVRs or ballot images, I can find her ballot and see how she voted.

9/ (b) Poll workers or election observers could similarly note the public counter value to target specific voters. They could also keep a complete record of who uses the scanner, in order, which would allow them to deanonymize all ballots cast at a precinct.
10/ (c) Some localities publish scanner log files from the ICP or ICE. These pose little privacy risk by themselves, but combined with the DVSorder vulnerability they reveal the exact time each ballot was cast. This provides an additional route to identify voters’ ballots.
11/ (d) A few localities even record surveillance video in polling places. This image is from a day-long video from Georgia, obtained by others via a public records request. If the locality releases vulnerable ballot images, anyone can link each ballot to footage of who cast it.

12/ The cause of the vulnerability is that Dominion uses a flawed random number generator to generate ballot IDs. When a ballot is cast, the ICP and ICE assign it a random-looking 6-digit id, which stays associated with the ballot even after CVRs or ballot images are shuffled.
13/ We were able to reconstruct the random number generator algorithm using only publicly available data. It turns out to be a lightly-obfuscated linear congruential generator, which experts have known for decades is unsuitable for security applications.
14/ Worse, the scanners essentially all follow the same fixed sequence of 1,000,000 ballot ids. It’s only the starting point in this sequence that’s randomized from one batch of ballots to the next.
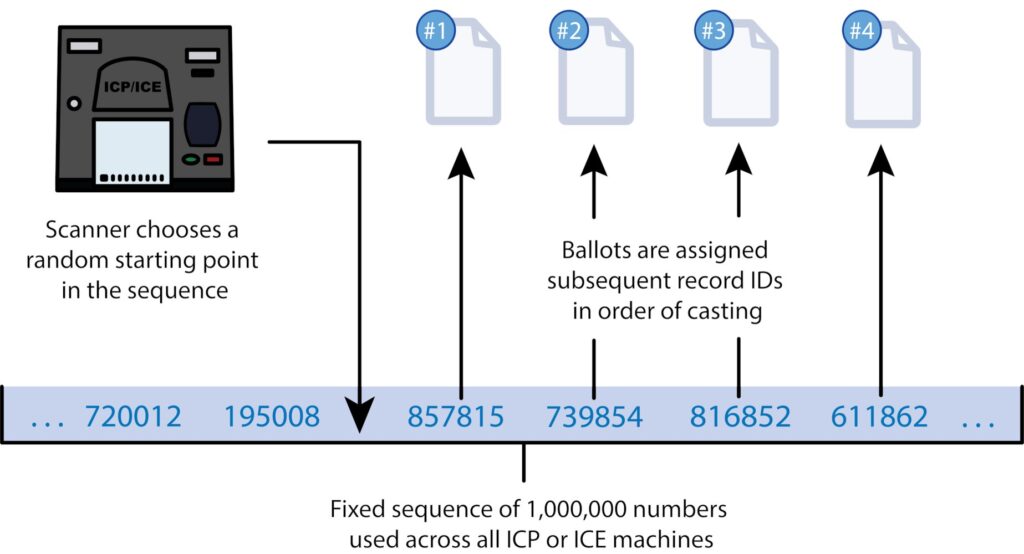
15/ This means that, given the set of ballot ids in a batch of CVRs or ballot images, it’s easy to find the ids in the fixed sequence, and this immediately tells you the order in which the ballots were cast.
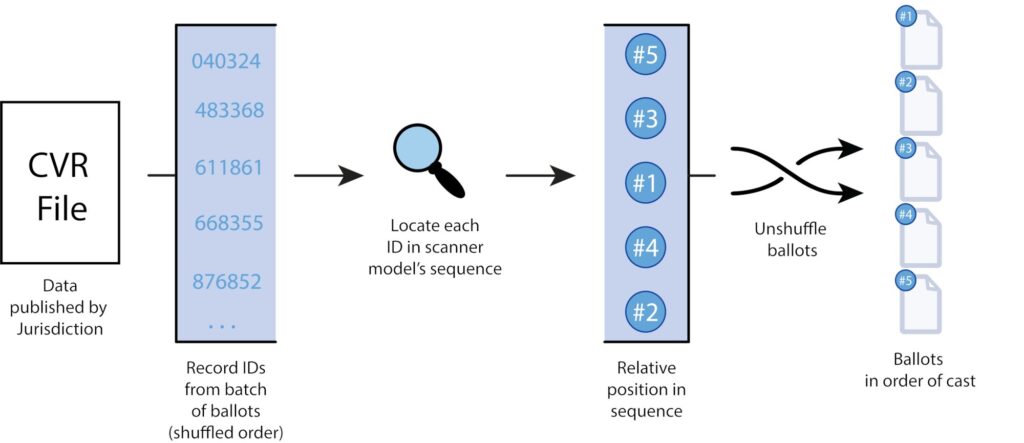
16/ Public access to election data, including cast-vote records and ballot images, can be valuable for voter confidence. Fortunately, mitigating the DVSorder flaw does not require reducing this transparency.
17/ Jurisdictions that use the Dominion ICP or ICE can prevent the vulnerability from being exploited by the public by “sanitizing” ballot-level data they publish to remove or encrypt the ballot record ids.
18/ We provide data sanitization instructions at https://DVSorder.org, and we’ve also created an open-source tool to help sanitize more complicated data formats and scenarios.
19/ We hope that Dominion will fix DVSorder in future software, releases, but once vulnerable ballot-level data is published, it remains susceptible to unshuffling in perpetuity, even if the scanners are eventually patched.
20/ That’s why we’re making our findings public now, to give election officials time to safely sanitize the data they release from the midterms. Our priority is to prevent this flaw from affecting voters this November, which is ultimately the best way to uphold public trust.
21/ For more information, please visit http://dvsorder.org. This research was conducted with
@braden_crimmins, @dhanya_nar, and @j_os_iah at the University of Michigan and Prof. @_aaspring_ of Auburn University. The diagrams above are by LaKyla Thomas.
22/ More from
Today my @UMich and @AuburnU colleagues are publishing info on a privacy flaw we’ve found in some U.S. voting machine models.
— Braden Crimmins (@braden_crimmins) October 14, 2022
The vulnerability, which we’re calling DVSorder, does NOT allow manipulation of votes or election results, but it could reveal how specific people voted.